ShadowDragon’s most recent podcast dove into the complexities of election monitoring and security. In this episode, special guest Bryeanne (Brye) Ravettine shared her insights into the world of election intelligence, the challenges analysts face in the digital era and what could be in store in the future. Brye, an intelligence analyst with over a decade […]
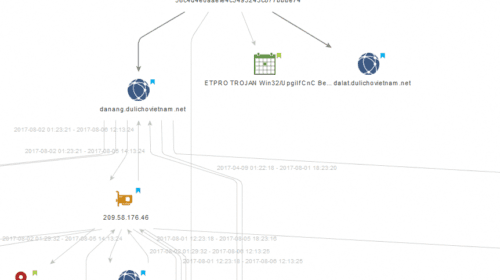
ShadowDragon – Maltego Transforms | Vietnamese Victims 1937CN
Votiro Labs and ClearSky CyberSecurity both based out of Israel, through use of MalNet have uncovered a slew of interesting TTPs and infrastructure believed to be used by the 1937CN […]
iHTAC Offers LE Resources to Help Children Victimized by Trafficking
Accelerating Law Enforcement Capabilities DeliverFund’s iHTAC is a unique collaboration with corporate partners who bring innovative technology tools used to accelerate law enforcement capabilities in their case work. The iHTAC […]
Tales from the Trenches: Assumptions & Out-of-Country Investigations
In one case, I found myself in a country in Latin America investigating a complicated persistent business compromise being implemented through both electronic and human means. I had already been […]
Artifacts, Speculation and Compromised Secrets
The buzz of cyber compromise has been booming since the AP released some interesting points on the Hillary Clinton email compromise. This was followed up by Brian Krebs on May […]
The Cyber Crime Chronicles: The Cyber Criminal
Perhaps the most nefarious, these attackers are driven almost exclusively by financial gain. These criminals typically target personal and corporate systems, and range in skill from Nigerian 419 phishers, to […]
MalNet Maltego Transforms with ProofPoint Data
MalNet accesses the Proofpoint ET Intelligence™ comprehensive database that contains current and historical malicious IP addresses and domains. In this blog post we share screenshots of Maltego 4 and a […]
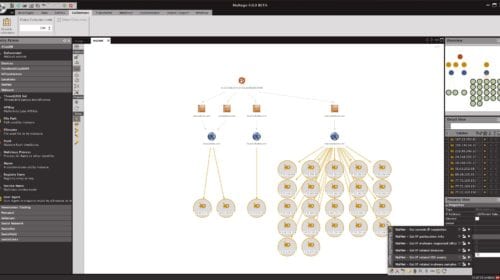
ShadowDragon Screenshots with Maltego M4 Release
Below are a few screenshots of our flagship product SocialNet, integrated with the new Maltego M4 release. If you haven’t seen the video from Maltego, please go check it out […]
OSINT Process, SocialNet and Breaking Bad Case Files
Our first artifact, begins with the email address rumored to be used by Jesse Pinkman, pivoting on one to one correlations between his favorite social media provider and others, we […]
Tracking GozNym Campaigns with MalNet
In 2007, Don Jackson while at SecureWorks had written about the Gozi Trojan, sharing details on the modularization and monetization strategies utilized by this family of malware. More recently, (04/04/16) […]
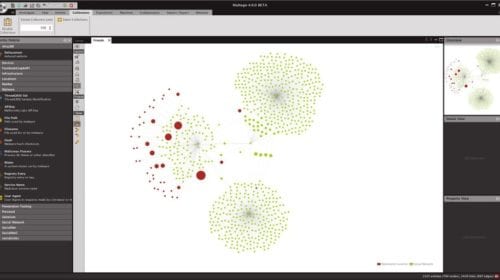
Demonstration: Tracking Malware Campaigns and Domains Using MalNet
MalNet brings together the industry’s most up to date and extensive threat information from Proofpoint with Maltego link analysis capabilities from ShadowDragon. MalNet enables threat analysts and researchers to identify […]
The Cyber Crime Chronicles: Your Friendly Neighborhood Hacker
Just a couple of weeks ago the world was rocked by the news that CIA Director John Brennan’s AOL email account (apparently that’s still a thing) had been hacked. Immediately, […]
The Cybercrime Chronicles: Understanding The Actors
Cyber Threat Types and Motivations There are several types of cyberwars going on at any given time. There are plain old hacking attacks, criminally-targeted attacks, nation state cyberwar, and hacktivist […]