MalNet accesses the Proofpoint ET Intelligence™ comprehensive database that contains current and historical malicious IP addresses and domains. In this blog post we share screenshots of Maltego 4 and a quick youtube video.
In this example, we cover 15 domains related to GozNym campaigns that operated in the month of April, 2016.
MalNet with GozNym
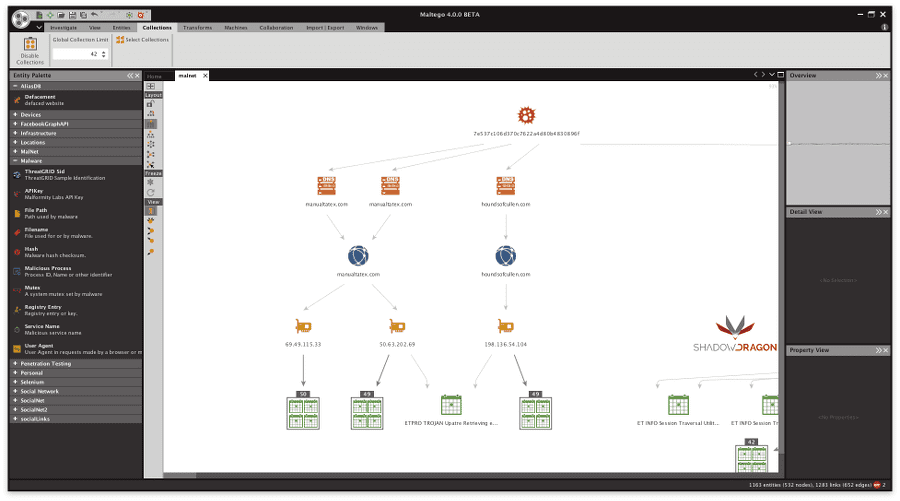
In the examples below, within the screenshots provided we cover malware associated with the domains manualtatex.com and houndsofcullen.com, identifying related malware, IP addresses, associated domains and IDS signatures related to traffic generated by malware.
Starting with a Hash
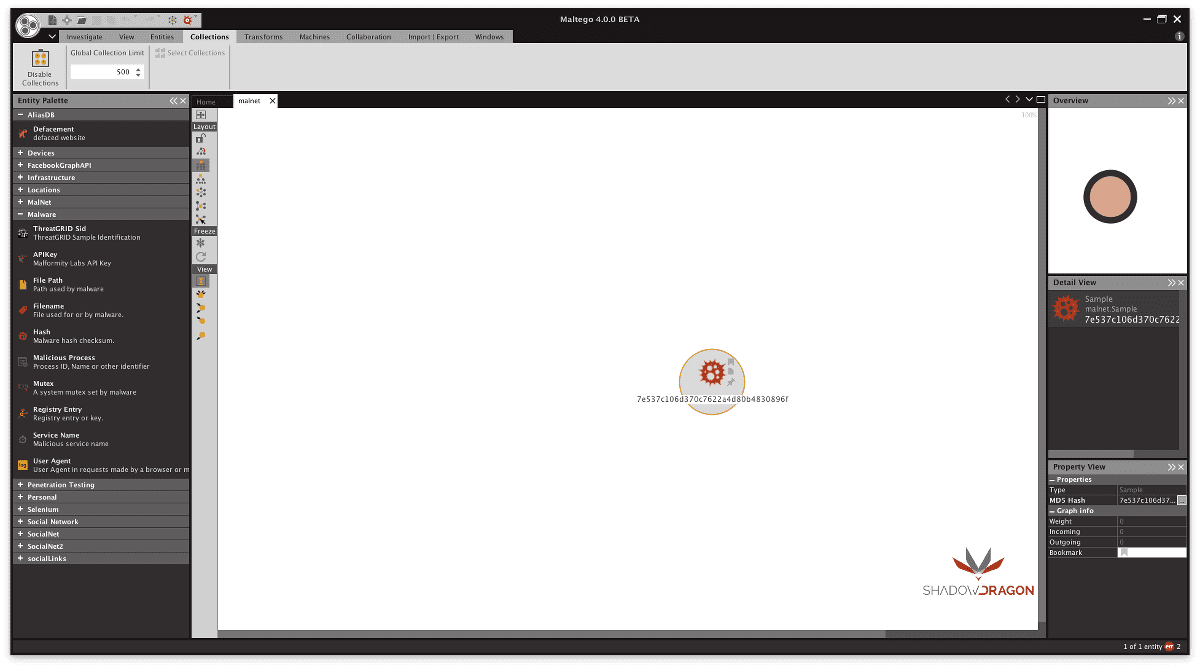
Get DNS Lookups

Acquire Related IP Addresses

Identify IDS Signatures Related to Malware Traffic
With the capability to track both physical and digital threats, ShadowDragon’s are valuable to most any security, cybersecurity, intelligence or law enforcement professional in support of:
- Visualize malware connections and campaigns into the 1000s of records
- Analyze data using 100+ commercially supported transforms
- Access industry leading current and historical Proofpoint ET Intelligence
- Connect specific attack campaigns to billions of available individual indicators
- Search and view attacks and actors in motion all over the world.
- Easily pivot and drill down with a forensic data trail for incident investigation.
- Correlate IDS Signatures to Malware for network based IOCs.

