Additional information is always needed on initial indicators for a SOC analyst or incident handler. In this case, initial indicators point to [ clear. co. ir and 79.127.125.179 ] engaging in exploitation like behavior or are operating as a drop point for other exploit artifacts.
What I want to know more of is the following:
- What other IOCs can I enumerate with this information?
- Can I produce other indicators, that I can place into network sensors or additional IOC/threat-hunting/intelligence reports?
- When did this campaign likely start based on malware samples observed?
- Are there any additional malware samples related to these two IP/Domains?
I am using MalNet – (Proofpoint Visualization within Maltego) [https://shadowdragon.io/product/malnet/] and assume you are familiar with link analysis.
Process
* Step 1 – Pivot on domain [ clear . co . ir ].
* Acquire Domain related malware-requested URLS
http:///<domain>.ir/wp-includes/SimplePie/HTTP/access/info/final.htm
http:///<domain>.ir/wp-includes/SimplePie/HTTP/access/info/access.php
http:///<domain>.ir/wp-includes/SimplePie/HTTP/access/info/log.htm
http:///<domain>.ir/wp-includes/SimplePie/HTTP/access/info/verify.php
http:///<domain>.ir/wp-includes/SimplePie/HTTP/access/info/index.htm
Observations:
Looking quickly at the Author information and html returned from /log.htm, an analyst can see “2017 JPMorgan Chase & Co.”. Likely a Chase Phish etc.
Step 2 – Pivot on domain of [clear. co.ir ], asking if any malware samples are related to this domain. This returns the following:
MD5: 105e6078e25d0c026188c4887d3139b4
First Seen: 2019-11-07
Last Seen: 2019-11-08
Submission Date: 2019-11-07 14:27:03
Observed From: Packet Capture
MD5: d11e8b7ad8327acf82bb5e5863de3e70
First Seen: 2019-11-07
Last Seen: 2019-11-14
Submission Date: 2019-11-07 14:46:05
Observed From: Packet Capture

Network Indicators (NIDS signatures) relating to this traffic also correlated to the following signatures:
ET CURRENT_EVENTS Chase Phishing Landing 2018-02-15 [SID 2823937]
ETPRO CURRENT_EVENTS Successful Chase Phish Sep 14 2017 [SID 2025366]
ET POLICY Http Client Body contains password= in cleartext [SID 2012885 ]
ET CURRENT_EVENTS Possible Chase Phishing Landing – Title over non SSL [SID 2025674]
ETPRO CURRENT_EVENTS Successful Generic Phish (302) Dec 16 2016 [SID 2827953]

Step 3 – Pivot on IP address 79.127.125.179 (Related to clear . co . ir). Query if the IP address has any other related domains associated with it in the past.

We now have a list of related domains to 79.127.125.179. Any traffic going to these domains or IP should be flagged, monitored or blocked.
electrosarmen . ir
galinbrand . com
hamedancouncil . ir
hamedsiadat . com
asimclinic . com
baroos-fam . com
I now want to get related malware samples observed on these related domains as well.
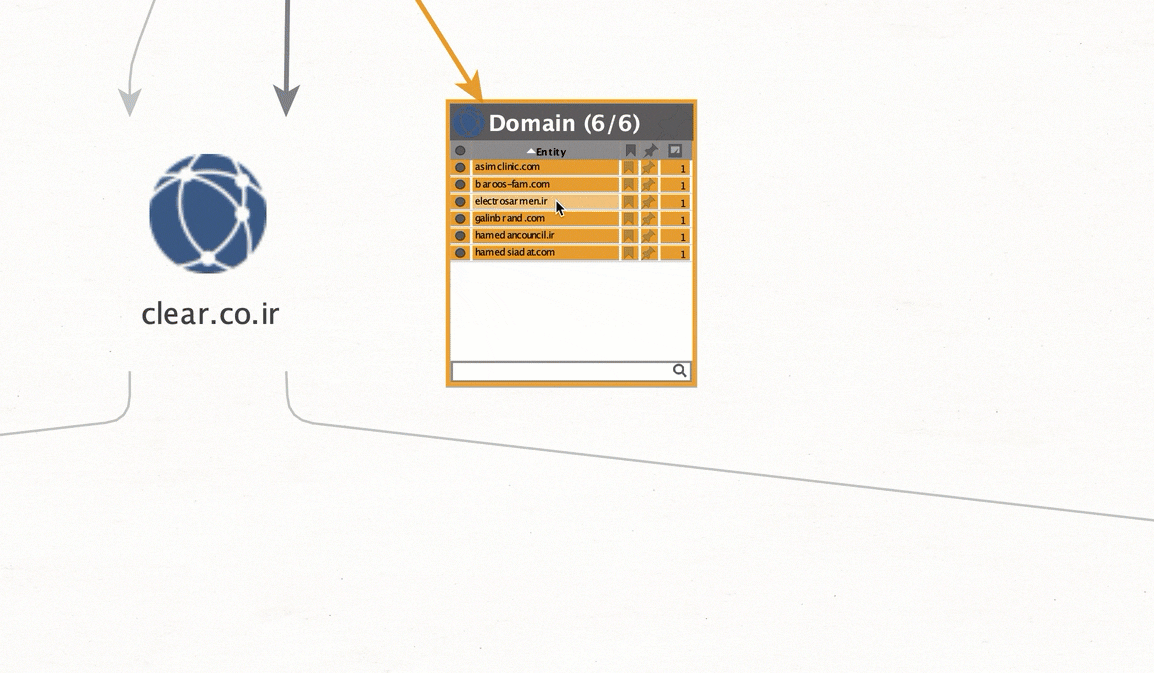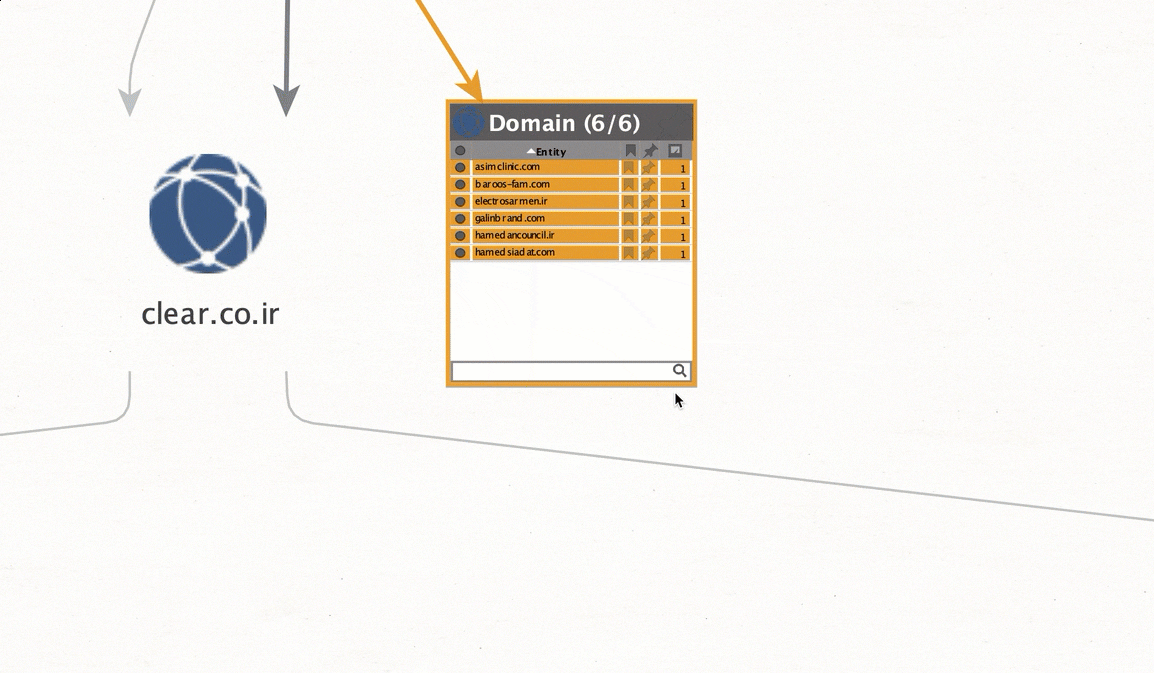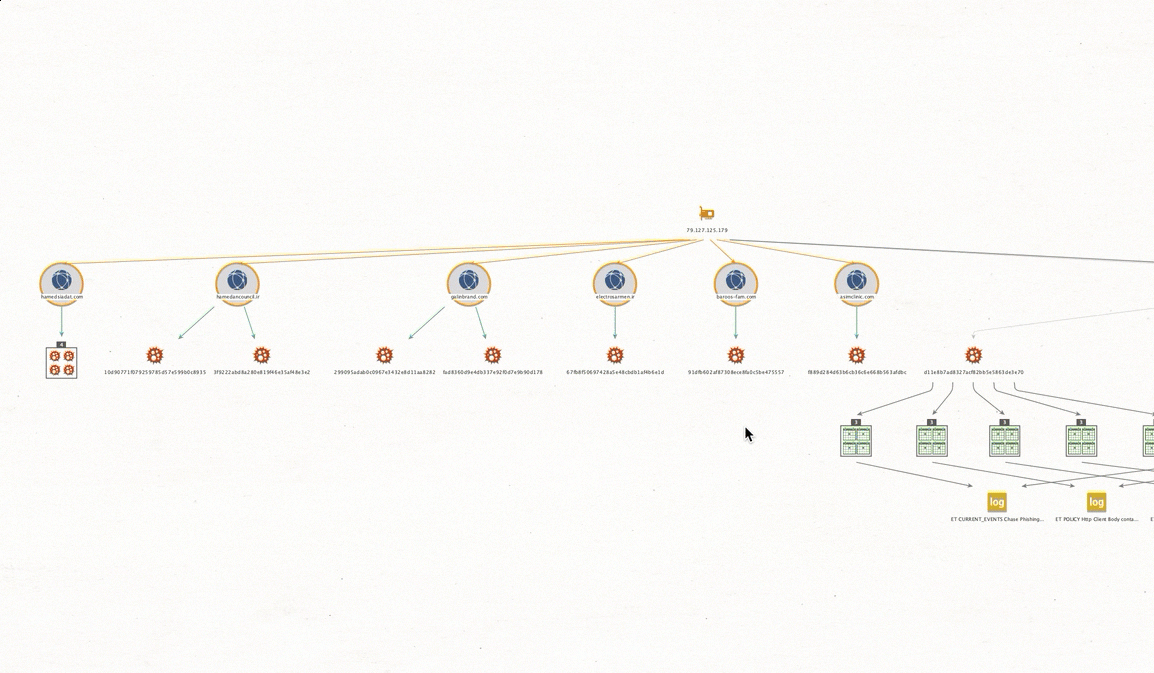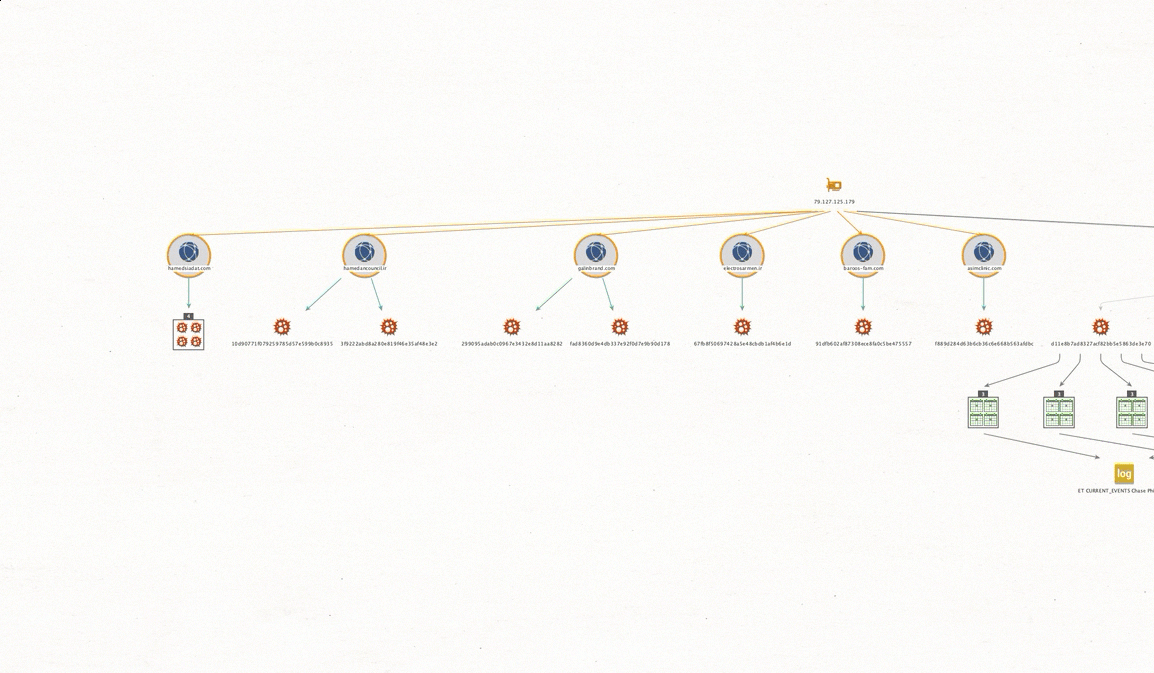
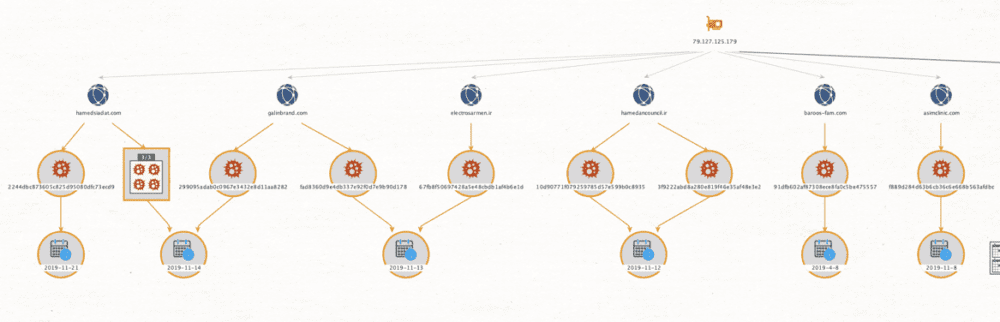
11 Additional pieces of malware are sited, showing that this IP and domains related to it have been used in prior attacks in the past. Some campaigns mapping back to 04/08/10 { Domain:baroos- fam.com , MD5: 91dfb602af87308ece8fa0c5be475557 }.
Complete correlated domains with mappings hosted on 79.127.125.179 include:
electrosarmen. ir [ Campaigns 11/13/19 ]
MD5: 67fb8f50697428a5e48cbdb1af4b6e1d
galinbrand. com [ Campaigns 11/13/19 – 11/14/19 ]
MD5: 299095adab0c0967e3432e8d11aa8282
MD5: fad8360d9e4db337e92f0d7e9b90d178
hamedancouncil. ir [ Campaigns 11/12/19 ]
MD5: 3f9222abd8a280e819f46e35af48e3e2
MD5: 10d90771f079259785d57e599b0c8935
hamedsiadat.com [ Campaigns 11/14/19, 11/21/19 ]
MD5: 2244dbc873605c825d95080dfc73ecd9
MD5: 62233dd1fb961a75f1c3b099e2c4d025
MD5: ea9b4acff2336630dcde6b9e8bc68721
MD5: dcfef8c42ac614c29e7a4c021aa68323
hamedancouncil. ir [ Campaigns 11/12/19 ]
MD5: 3f9222abd8a280e819f46e35af48e3e2
MD5: 10d90771f079259785d57e599b0c8935
hamedsiadat.com [ Campaigns 11/14/19, 11/21/19 ]
MD5: 2244dbc873605c825d95080dfc73ecd9
MD5: 62233dd1fb961a75f1c3b099e2c4d025
MD5: ea9b4acff2336630dcde6b9e8bc68721
MD5: dcfef8c42ac614c29e7a4c021aa683232
asimclinic.com [ Campaigns 11/08/19 ]
MD5: f889d284d63b6cb36c6e668b563afdbc
baroos-fam.com [ Campaigns 04/08/19]
MD5: 91dfb602af87308ece8fa0c5be475557
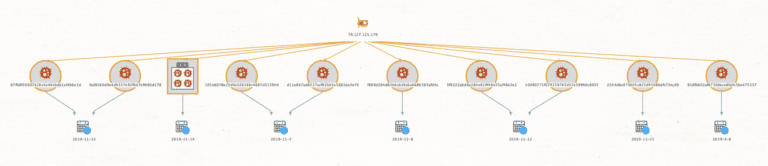
We next want to go back to pivoting on 72.127.125.179 and ask “What Malware Hashes have historically been associated with this IP“. (Just for completeness, we see the same information repeated).
MD5's Associated:
10d90771f079259785d57e599b0c8935
3f9222abd8a280e819f46e35af48e3e2
f889d284d63b6cb36c6e668b563afdbc
105e6078e25d0c026188c4887d3139b4
d11e8b7ad8327acf82bb5e5863de3e70
91dfb602af87308ece8fa0c5be475557
2244dbc873605c825d95080dfc73ecd9
62233dd1fb961a75f1c3b099e2c4d025
dcfef8c42ac614c29e7a4c021aa68323
299095adab0c0967e3432e8d11aa8282
ea9b4acff2336630dcde6b9e8bc68721
67fb8f50697428a5e48cbdb1af4b6e1d
fad8360d9e4db337e92f0d7e9b90d178
We now want to identify all of the unique IDS signatures that span across all known pieces of malware that have been identified. This will serve as backscatter traffic, you will want to observe over the network
ET POLICY Possible External IP Lookup www.whatsmyip.us
ET POLICY Possible External IP Lookup www.whatsmyip.us
ETPRO CURRENT_EVENTS Terse POST to WordPress Folder - Probable Successful Phishing
ETPRO CURRENT_EVENTS Successful Generic Webmail Phish 2019-06-10
ET POLICY Possible External IP Lookup www.whatsmyip.us
ET POLICY Possible External IP Lookup www.whatsmyip.us
ET POLICY Possible External IP Lookup www.whatsmyip.us
ETPRO NETBIOS Microsoft Windows Active Directory BROWSER ELECTION Buffer Overflow Inbound Netbios 138 1
ET SHELLCODE UTF-8/16 Encoded Shellcode
ETPRO CURRENT_EVENTS DHL/Adobe/Excel Phishing Landing Jan 05 2016
ETPRO CURRENT_EVENTS Fedex Javascript Phishing Landing Sept 8 2016
ETPRO CURRENT_EVENTS Possible Successful Generic Phish Aug 31 2015
ETPRO CURRENT_EVENTS Successful OneDrive Phish 2018-04-16
ETPRO CURRENT_EVENTS Successful Chase Phish Sep 14 2017
ET CURRENT_EVENTS Generic Multi-Email Phishing Landing 2018-08-30
ET INFO Suspicious HTML Decimal Obfuscated Title - Possible Phishing Landing Apr 19 2017
ETPRO CURRENT_EVENTS Generic 302 Redirect to Phishing Landing
ETPRO CURRENT_EVENTS DHL Phishing Landing Jan 05 2016
ETPRO CURRENT_EVENTS Successful OneDrive Phish 2018-04-16
ET POLICY Http Client Body contains password= in cleartext
ETPRO CURRENT_EVENTS Secure Cloud Files Phishing Landing 2018-01-10 M1
ETPRO CURRENT_EVENTS Successful Generic Webmail-Mini Phish 2018-09-21
ET CURRENT_EVENTS Possible Chase Phishing Landing - Title over non SSL
ETPRO CURRENT_EVENTS DHL Phishing Landing Jan 05 2016
ET CURRENT_EVENTS Possible Compromised WordPress - Generic Phishing Landing 2018-01-22
ETPRO CURRENT_EVENTS Secure Cloud Files Phishing Landing 2018-01-10 M2
ETPRO CURRENT_EVENTS Secure Cloud Files Phishing Landing 2018-01-10 M1
ETPRO CURRENT_EVENTS Successful Generic Phish (302) Dec 16 2016
ETPRO CURRENT_EVENTS Secure Cloud Files Phishing Landing 2018-01-10 M2
ET POLICY Http Client Body contains pass= in cleartext
ET CURRENT_EVENTS Generic Multi-Email Phishing Landing 2018-08-30
ET POLICY Http Client Body contains password= in cleartext
ETPRO CURRENT_EVENTS Possible Successful Generic Phish July 28
ET CURRENT_EVENTS Generic Multi-Email Phishing Landing 2018-08-30
ET INFO Suspicious HTML Decimal Obfuscated Title - Possible Phishing Landing Apr 19 2017
ETPRO CURRENT_EVENTS Successful Generic Webmail-Mini Phish 2018-09-21
ET CURRENT_EVENTS Possible Compromised WordPress - Generic Phishing Landing 2018-01-22
ETPRO CURRENT_EVENTS Generic 302 Redirect to Phishing Landing
ETPRO CURRENT_EVENTS Successful Generic Phish (302) Dec 16 2016
ETPRO CURRENT_EVENTS Successful Generic Webmail-Mini Phish 2018-09-21
ETPRO CURRENT_EVENTS Successful OneDrive Phish 2018-04-16
ETPRO CURRENT_EVENTS Generic 302 Redirect to Phishing Landing
ET POLICY Http Client Body contains password= in cleartext
ETPRO CURRENT_EVENTS Possible Successful Generic Phish July 28
ET POLICY Http Client Body contains password= in cleartext
ET CURRENT_EVENTS Chase Phishing Landing 2018-02-15
ETPRO CURRENT_EVENTS Possible Successful Generic Phish July 28
Looking at all of this information in real time… Here is the video.
Any tool that helps me move from zero knowledge to more knowledge is valuable, especially during an incident where I may need to augment looking for IOCs in an environment or task others with watching for things on the wire.

