We’ve all heard the advice a million times, “Don’t use the same password on different websites.” Unfortunately, (or fortunately, depending on our motivations) many users make this exact mistake. In 2019, the top 10 most common passwords are things like “12345” or “password,” and the number of accounts out there with a sports team or band name as the password is unreal. Humans are very predictable.
Why are we interested in passwords today? Many times, when I’m working through an investigation of a target, I start my search off with an email. One of the great things about having a target’s email is, unlike an alias, the email provides a 1-to-1 correlation to the target and an online profile. I’d venture to guess that, outside of the blue check-marked realDonaldTrump on Twitter, all of the other “realDonaldTrump” accounts throughout the internet are probably not really the REAL Donald Trump.
If we can correlate an email to a specific online account, that gives us a much better chance that the account we are looking at is indeed the target’s actual account. While this information is great, what if the email we are starting with doesn’t correlate to any account we can find? This is where the password fun comes into play.
We know that people are generally lazy with passwords and many times will use the same password or a version of the password with many online accounts. How can we leverage this to get us more information on our target?
Let’s walk through uncovering more email addresses a target might have based on password reuse. I’ve picked a random email address from a large data breach as an example. To mitigate doxxing this poor guy, I’m going to be showing only part of the address.
My first search in SocialNet with our starting email yielded no online accounts associated with the email. A few quick web searches also turn up nothing. However, the email is part of a large data breach.

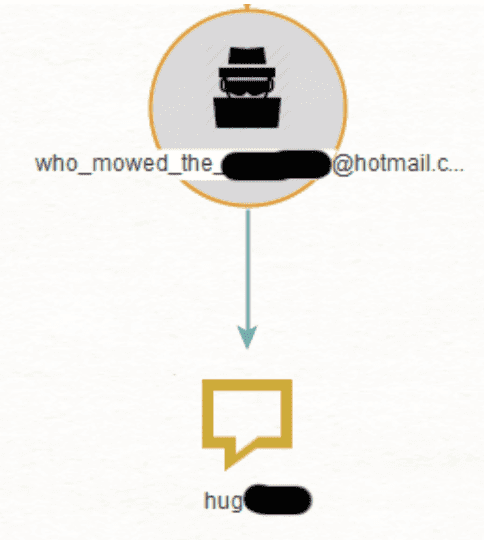
Let’s get the password from the breach it was a part of.
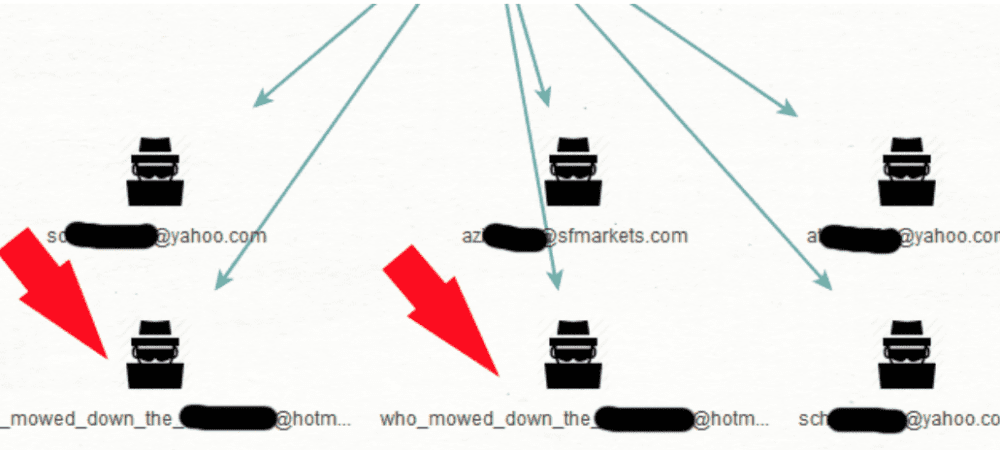
Now that we have the password, let’s search for other emails in the data breach.

Oh, yeah! We’ve got 6 emails that all used that password. Including the two I’ve highlighted that are VERY similar to the one we started with. This is a great indicator that this is the same person. Let’s try searching with our newly found email.

As you can see, we found a couple of Skype accounts, and we were able to get the alias off of those accounts. With our newly uncovered alias, we were able to quickly identify our target’s Instagram, Twitter, Xbox, Twitch, Spotify, and Reddit.
What are some takeaways from this little adventure? First of all, for good operational security, don’t reuse passwords. Secondly, the idea of hacking into accounts with the passwords we find here isn’t our goal. In the world of OSINT, a password from a breach is something that can easily be overlooked as vector to get us to the next step in our investigation. Don’t miss that step by ignoring this powerful concept. Happy hunting.