As a follow up to our last blog about password reuse and the recent data breach of Disney, I would like to talk about how to create strong passwords and why they are “strong.” Typically, we like to use passwords that are easy to remember and/or have some personal significance to us. The most popular passwords we have seen are “password,” “password1,” “12345,” etc. Other typical passwords that are chosen are some form of the username/password that they used for their login. There are also passwords that contain the season the password was created in, etc.
## What is in a Password
We use passwords every day but generally never give them a second thought. Passwords contain anywhere between 6-16 characters, mostly “ascii”; this includes upper- and lower-case alphabet letters, numbers, and symbols. That means there are between 6^70 and 16^70 possible passwords. However, most people will choose common words or words that have meaning to them, words like the names of their children, or the name of a significant other. This drastically narrows down the number of possible passwords there could be. That is where password cracking comes in.
## Real World Example
Let’s take a password that we can tell is very popular, like “correcthorsebatterystaple.” We can run that through our tools and it pops out the following entities:
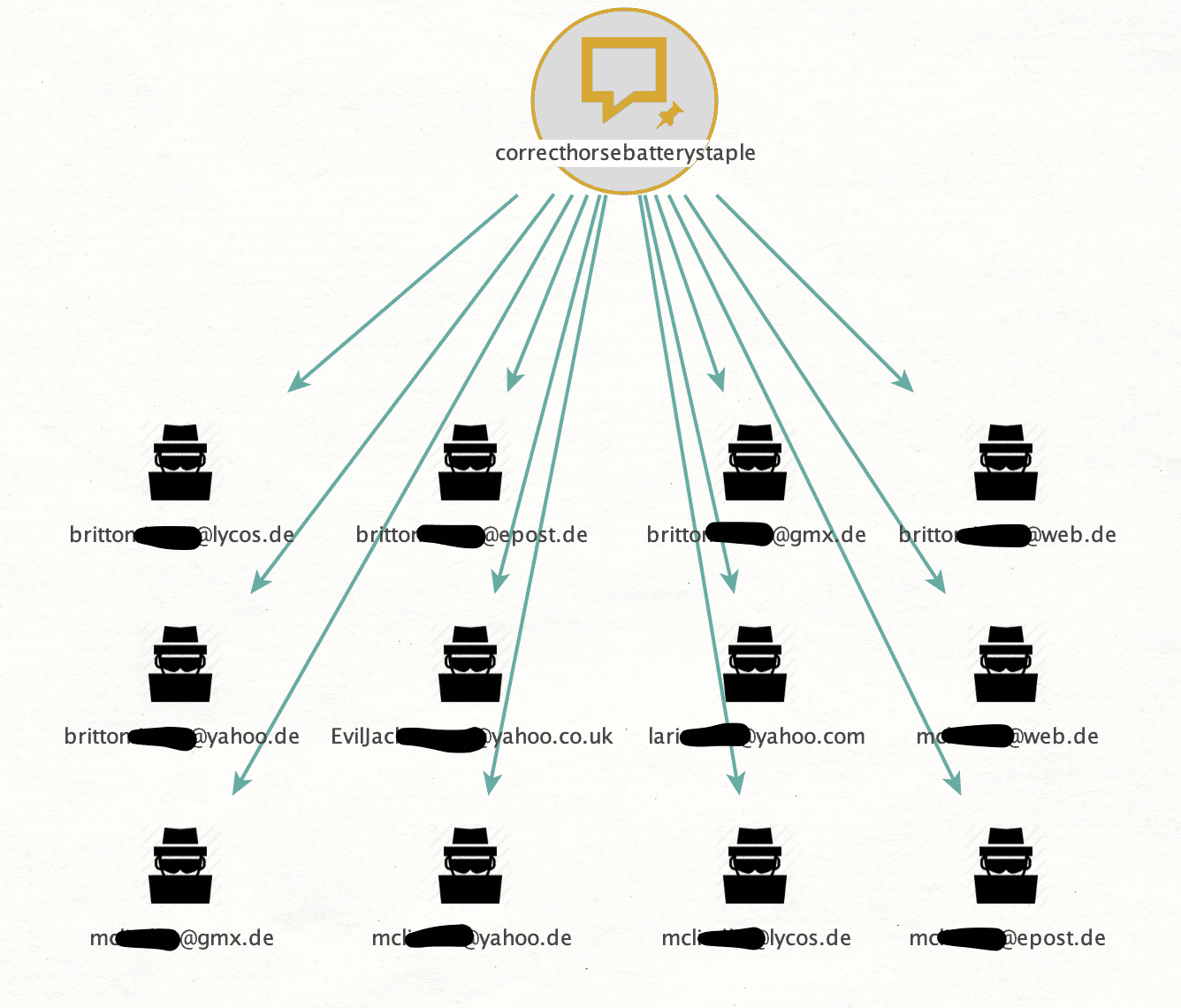
Notice that “britton” has several different accounts all using the same password. Same with “mcli…” This is a real world example of where people reuse the same passwords for multiple sites!
## How Password Cracking Works (Kinda)
AS stated above, there are **A LOT** of possible passwords out there; if you do the math, billions of billions. But people are predictable and tend to use easy-to-guess passwords. We also tend to reuse passwords we know. In our database, we see password reuse happen all the time. We also do not tend to see very complicated passwords. Typically, we see a common word with a letter appended to it; sometimes the first letter is capitalized, depending on the password rules the site has. Given that there are only so many words in that fit into the english language (and make sense), hackers can just build up massive list of words, called “rainbow tables,” and just try each one to see if it is your password. Using rules to enumerate the different ways people may change the password, a hacker can most likely guess your password.
### How Hackers Get Passwords
Man-in-the-middle. When you interact with any network, the packet you send can be monitored, either by a person you trust, like your ISP, or someone you do not, like a hacker. There really isn’t a way around this, but you can use some basic security techniques to keep your packets from being used against you. HTTPS, SSL, and the like are good things. Hackers can also use basic techniques (SQL injection, Cross-Site scripting, etc.) to dump databases of user information. If the database stores your password in plain text, then they have it and may just share it with the world. Other times, the passwords are hashed, and that is where the previous section comes into play.
### Hashes
Hashing is the name for when your password is turned into an unrecognizable string of letters and numbers. The basic idea behind a hash is to turn a string into a number. This number is very big and _usually_ is unique. They are also very difficult, in not impossible, to reverse. So very smart people have decided that hashing passwords is typically enough when it comes to storing your password in a database. Instead of trying to reverse the hash, hackers will simply use the techniques described above to check randomly generated passwords against your password hash. Using a single machine, testing the billions (literally) of possible passwords would take a LONG time. So hackers will build cracking stations made of several machines, each of which runs several graphics cards and each of which can do several thousand (at least) hash calculations and comparisons per second.
## HashCat Example
Below is an example of how the popular hash cracking software, “hashcat,” can brute force passwords. This session was completed in about 18 minutes on a moderately sized gaming rig.
b3d8e741e5f9dd185a1f690e4ff510cd:90cdb6a1fc30:c0bdd181e398:Chunky:dannya02
5977f19fd3c79702a9fde49e66bd4db0:90cdb6a1fc30:d831346442a8:Chunky:dannya02
9959b5e9531490ed4ceb17696a852910:90cdb6a1fc30:f4afe7b34a3a:Chunky:dannya02
9e5129aa9a7a1ead592982c381a5e7d8:90cdb6a1fc30:f83880d809bc:Chunky:dannya02
825ec144cd5d774c953a573383ff8d7e:90cdb6a1fc30:d831341f24d9:Chunky:dannya02
3d6d83868db2f5ee83002b1196ccc5db:90cdb6a1fc30:1c1ac08f5ae2:Chunky:dannya02
5c76c29f85d3b5d616b7f18fb1fb1bd0:90cdb6a1fc30:6cadf8997f80:Chunky:dannya02
5caf1e2624da5a9618801625d4bf71c6:90cdb6a1fc30:1c1ac08f5ae2:Chunky:dannya02
[s]tatus [p]ause [b]ypass [c]heckpoint [q]uit =>
Session……….: hashcat
Status………..: Running
Hash.Type……..: WPA-EAPOL-PBKDF2
Hash.Target……: .pcaps20003_1576557971.hccapx
Time.Started…..: Tue Dec 17 12:31:49 2019 (17 mins, 50 secs)
Time.Estimated…: Fri Dec 20 04:32:10 2019 (2 days, 15 hours)
Guess.Base…….: File (E:weakpass_2_wifiweakpass_2_wifi)
Guess.Mod……..: Rules (rules/best64.rule)
Guess.Queue……: 1/1 (100.00%)
Speed.#1………: 784.5 kH/s (10.49ms) @ Accel:128 Loops:64 Thr:64 Vec:1
Recovered……..: 8/10 (80.00%) Digests, 0/1 (0.00%) Salts
Progress………: 838926336/180757382729 (0.46%)
Rejected………: 0/838926336 (0.00%)
Restore.Point….: 10584064/2347498477 (0.45%)
Restore.Sub.#1…: Salt:0 Amplifier:43-44 Iteration:3520-3584
Candidates.#1….: ma1mb090 -> maot7sj8
Hardware.Mon.#1..: Temp: 65c Fan: 0% Util: 99% Core:1770MHz Mem:6800MHz Bus:16
“`
## What you can do
Don’t reuse passwords. Don’t use single word passwords. Don’t make your password the same as your username. Do use a password manager to store your passwords. Do change your password from time to time.

