ShadowDragon’s most recent podcast dove into the complexities of election monitoring and security. In this episode, special guest Bryeanne (Brye) Ravettine shared her insights into the world of election intelligence, the challenges analysts face in the digital era and what could be in store in the future. Brye, an intelligence analyst with over a decade […]
Introducing ShadowDragon’s Horizon Monitor.
We are excited to announce a game-changing enhancement to our Horizon intelligence platform: Horizon Monitor. This represents a significant leap forward, seamlessly integrating with our existing world-class OSINT link analysis, […]
ShadowDragon Partners with SynapseAi to Expand Influence in Asia Pacific
Hoover, AL – [26th June] – ShadowDragon™, a provider of ethical open-source intelligence (OSINT), unique datasets and APIs, is pleased to expand its partner ecosystem through a strategic partnership with […]
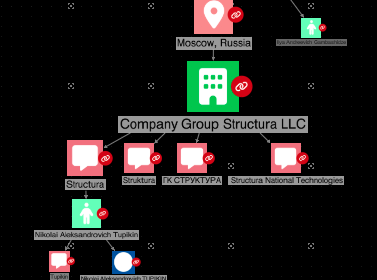
The G7, More Russian Sanctions, and a Warning
Nations met in Italy at a tense G7 Summit while the US Treasury levied more sanctions against Russia and Russian entities. The private sector must be vigilant to secondary sanctions […]
Building Trust in a Security Landscape
Trust underpins successful relationships, whether they are personal or professional, between businesses and customers, employers and employees, or organizations and their stakeholders. As digital transformation accelerates, the mechanisms to establish […]
OSINT Due Diligence: Enhancing Business Resilience in a Geopolitical Landscape
The need for deeper insights through due diligence is a must as modern businesses evolve with the changing landscape of compliance needs. Invisible lines are being drawn through sovereign borders […]
Words Matter: Open-Source Intelligence for the Private Sector
The military and intelligence community are run by strict sets of doctrine, authorities, regulations, instructions, directives… the list goes on – this is not the same for the private sector. […]
Link analysis with OSINT, breach data, and intelligence in one comprehensive investigations toolkit
In a landscape where information is power, the ability to gather, analyze, and act upon open-source intelligence (OSINT) is paramount for organizations across all sectors. Recognizing this need, we have […]
Bear Hunting: Mitigating Russian Sanctions Risk with OSINT
Since Russia’s invasion of Ukraine in February 2022, the multilateral Russian Elites, Proxies, and Oligarchs (REPO) Task Force has immobilized approximately $300 billion worth of Central Bank assets. Russia will […]
ShadowDragon Wins 2024 Frost & Sullivan Best Practices Award for Excellence in Global Open-Source Intelligence
As a pioneer of open-source intelligence (OSINT) investigation tools dating back to 2009, ShadowDragon is honored by a recent award recognizing us as a transparent and reliable vendor that supports […]
ShadowDragon Enters Strategic Partnership with Collaboraite and Vestigo to Build Trust in OSINT
Global leaders in open-source intelligence and operational security partner to foster trust in data and technology HOOVER, ALABAMA – March 4, 2024 – ShadowDragon™, a provider of ethical open-source intelligence […]
The (Un)hidden Threat: Child Grooming on Social Media
Technative generations do not know life without the internet and even my one year old niece knows how to navigate a device. Whilst screen time can be good for learning […]
ShadowDragon Commentary: Rethinking Open-Source Intelligence for Security in Commercial Settings
Recently, ShadowDragon COO, Jonathan Couch, contributed an article to InfoSecurity Magazine on thepotential for open-source intelligence (OSINT) to bolster security efforts within the private sector. In thispiece, Couch reflects on […]