I had previously written about how we started with our our monitoring platform and how that grew into the beast it is today. I didn’t leave much room to frame things in the most hip-infosec way, rattling off buzz words of deep-dark-web-monitoring or deep dark interwebs monitoring.
Sometimes asking the right questions on new technology can be tough. There are many loud voices in the space and many will use naming conventions which make things sound newer and more advanced than they are. In this vein, I will share some thoughts on what is important when deciding to monitor risks, chatter and content that exists outside of your network.
The last few years have been interesting watching the market evolve in the way they frame up “real time situational awareness” into different categories. Some call it “Dark Net Monitoring“, others call things “Deep Dark Web Monitoring“. Then there are the “Digital Risk Protection” (DRP) framers and the historical “Threat intelligence Platform” (TIPS) [2012 – Fwd]. Confusing and frustrating, but the industry secret… It doesn’t matter. All of these different naming conventions are just another way to describe a system where information outside of your network or even within a given marketplace or communication platform exists and needs to be monitored, and your team needs to be alerted if something is identified of interest.
It needs to be monitored for various reasons. Some of these reasons could be for brand protection, others could be to identify and thwart fraud rings, still others could be human trafficking or counter terrorism.
Things You Should Ask For (Behind the Scenes)
Even if monitoring is in place it won’t benefit you very well unless you have control over a few things. The key things you need to concern yourself with include the following:
- Do I get full content or metadata? (Always ask for one or the other).
- Are the collectors written to some type of spec? E.g. There is a vast difference on dialogue protocols (Chat), versus a stateless protocol (HTTP).
- Does this tool allow the analyst to collect at scale and can the solution help my analyst? How fast can new collectors be created?
- Does the solution have an API? If you wanted the solution to only collect and not act, has it been designed in an agnostic manner to enable duel use?
A secondary concern/theme I try to remind folks about is how well have the defined their process for monitoring and response and further monitoring refinement and action. You can monitor things across multiple platforms in a broad spectrum or a very narrow window. What are your goals?
Do You Have A Process?
With goals, this implies a level of maturity of the team not only in incident response, but also within the analytical process. Our overall security monitoring followed this process:
- Identify where information is being talked about, enabling monitoring of specific areas of interest.
- Identify what needs to be observed. For our clients, we needed to identify three different things: common sentiment, targets by the collective group and new capabilities. For each new capability, we needed to evaluate it and create signatures to detect the observed attack tools.
- Write a daily brief, as formatted above with monitoring.
Identifying your maturity level is key in having a pattern of detection, reaction, and adjustment to ongoing monitoring needs across the business. Demand a process even if it is a bullet point process.
Beware of Hype versus Tactical Value
What isn’t as helpful are the following items:
- Sentiment Analysis. Hipster analyst like to say they have sentiment analysis. Sure, it is cool and NLP is rad.. but how helpful is it? If you are monitoring a language that will introduce many idioms, emojis or will change on a frequent basis sentiment analysis might not be valuable. You only have so many analyst cycles to spend. Combined AND, OR, NOR, NOT combinations are usually more helpful.
- Heatmaps. Ohhh, the heat maps and the crap maps. Thank you Norse and others. Sadly, a heat map function in most scenarios is largely inaccurate, but looks sexy-sexy-sexy. While functional use is low it does make things look pretty and when was the last time an analyst was fired over bad intel versus an ugly report?
Moving through the process and past the hype you will find yourself enjoying getting heads up alerts and writing a good report for your boss. Personally, I enjoy dragging screenshots out of our platform into reports.
On the concluding note, I will share a few screenshots from our monitoring platform that have been fun, enlightening and concerning at times. From OIMonitor and the screenshot engine within…
On average, with the DarkNet collector in OIMonitor we archive off somewhere between 60,000-90,000 sites a day. Here are some snapshots from that particular collector. I will post more data from our other collectors with features in followup posts.
Fake Ids, fake Currency For Sale

Art Forgeries For Sale

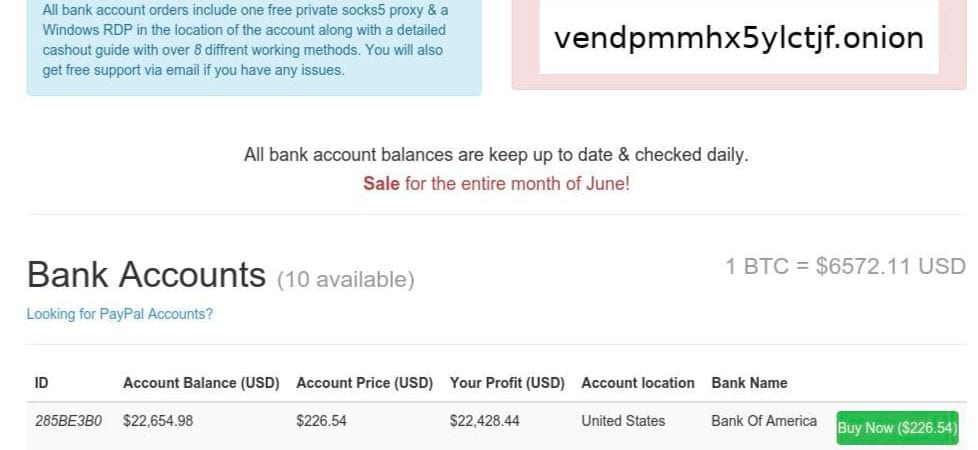
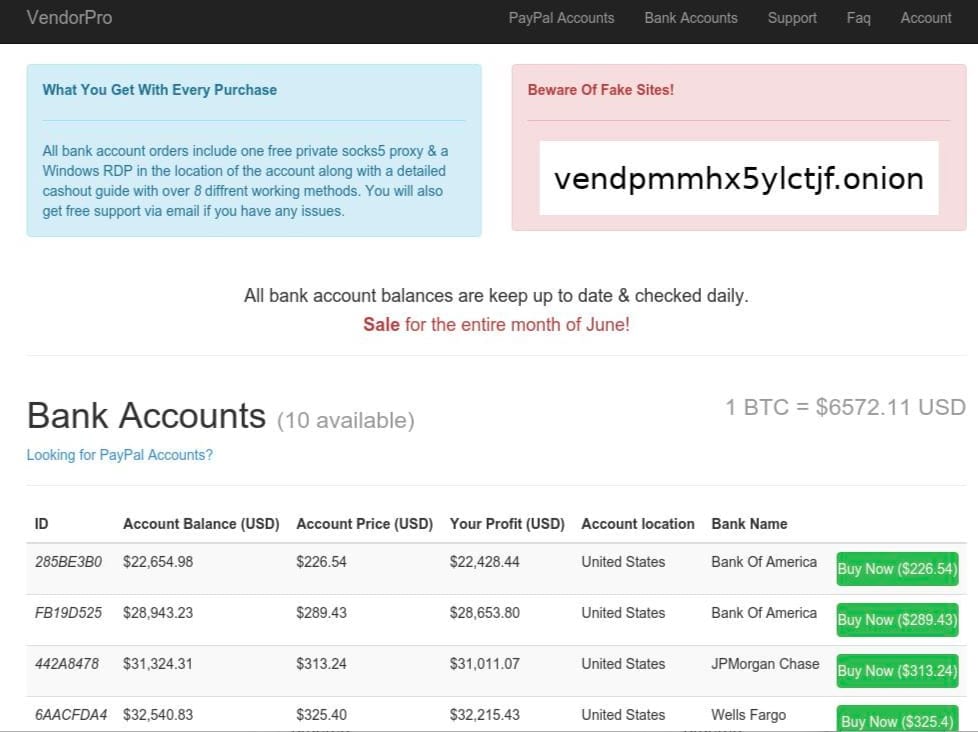
Bank Accounts with Balances For Sale
Credit Cards / Debit Cards / Super Affordable Gift Cards

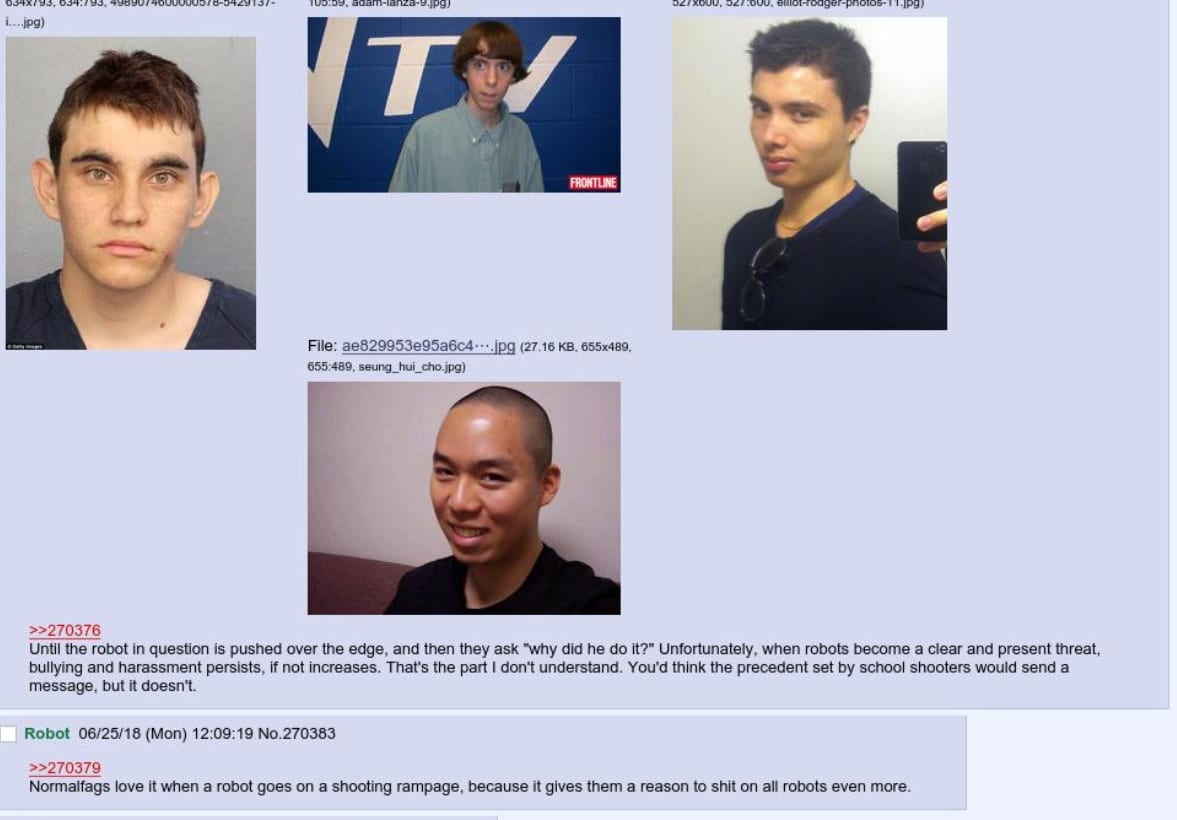
Forum Monitoring on School Shooting Chatter