In the past, we have looked into a hacker who comes from Iran by the name of Mrb3hz4d. Now if we take some of the information we saw from his defacement, we can create an extremely simple OIMonitor project to monitor and watch for other defacements and base it on region as opposed to individual attackers.
The obvious thing here is that a lot of up and coming attackers, especially those doing defacements, have some sense of pride for where they come from. A lot of them will reference what country they are from in their attacks, so we can use that to watch for attacks coming from specific regions.

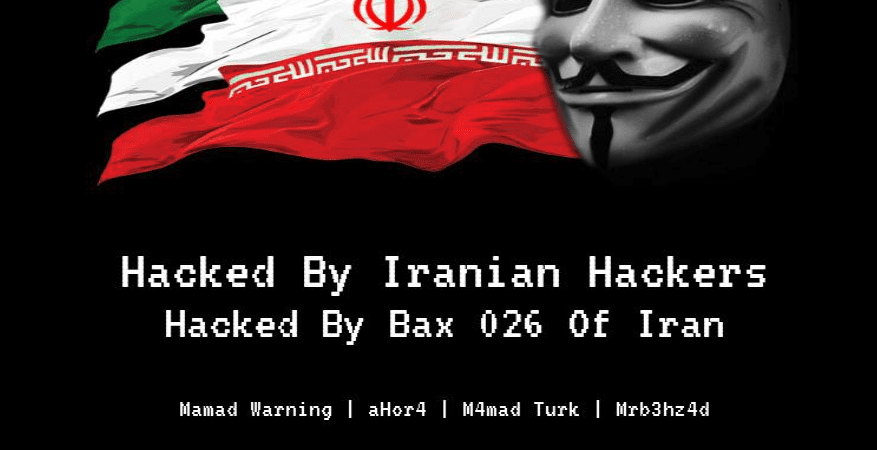
Above, we can see that our defacer “Bax 026” has that typical sense of national pride and is kind enough to let us know where he is from. We can also see that he is not a part of this hacking group, but it would seem like he is trying to become a member of it. That is just a bonus thing to note that we can use later as we see more and more content coming from “Bax 026”.
Above, we can see another example of this: a hacking team with a sense of pride with Iran… there is probably an exploitable pattern here. We can also start to see some overlap of one of the members. In Shield Iran Team, we have member Ro0t_ahor4, and in the team Iranian Hackers, we have member ahor4. Odds are this is probably the same person.
So let’s look now at how easy it is to monitor for just attackers in a handful of countries in the Middle East. We can start with three of them: Saudi Arabia, Iran, and Iraq.
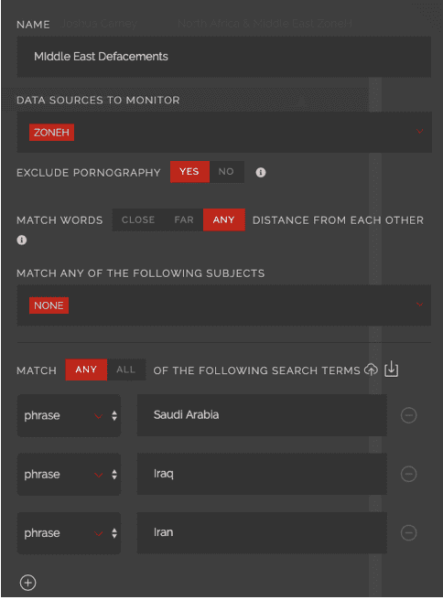
Here we have a very basic setup for an alert for monitoring for mentions of these national pride attackers. We are going to monitor specifically Zone-H, because it will give us more insight than just what was defaced. We can see how they defaced it and when. This allows us to create a timeline and show the evolution of the defacers by seeing the new and evolving exploits they are using. All of the examples seen here came from this project where we are tying attackers to regions.
Using OIMonitor alone, we are able to monitor for new defacements, look at the historical timeline of defacements based on various categories such as region, content, attackers, and many others. In addition to these two, we can see the growth of these attackers and groups, and see exactly how they are exploiting these sites, all with 3 phrases and about two minutes of setup.