Earlier this week FireEye/Mandiant had released a blog entitled “Insights into Iranian Cyber Espionage”
detailing the targets within the Aerospace and Energy sectors being targeted. To compliment their post we wanted to use our tools to track down additional information relating to online identities and infrastructure used by the actors as well as identifying additional IOCs or TTPs on the malware indicators shared.
Starting where Fireeye had left off in their post we pick up with some of the indicators shared:
-
-
Source of Email Sender – solevisible [@] gmail.com
-
-
-
Alias utilized “xman_1365_x”
-
-
-
Domain Masquerading
-
-
-
IOCs & C2s related to APT33
-
Immediate questions
Can we tie any of these aliases OR email addresses to IRAN?
One of our standard procedures to understand a threat actor better is to start the process of building a dossier. Email addresses and aliases are a great indicator to pivot on and see what other things we may be able to find across the internet or publicly accessible information. In this case, we want to look into the email address Fireeye had mentioned:
“solevisible [@] gmail.com”
Email addresses are helpful for a few reasons for investigative uses. Email addresses over time have been integrated into many online platforms to be utilized as a username. If we can correlate the email address to some other internet profile, maybe we can glean more information to help us build our dossier, or to understand the threat actor a bit better. The second item of interest is the alias “solevisible” attached to gmail.com. Even if we can’t find a good one to one correlation on this email address, the alias can also be used as a backup to dig further. Taking the email address as our first artifact to discover with SocialNet we find a few interesting things.
The email address in use had a direct correlation to an online social media profile on GooglePlus+, linking to an account name advertised as “Sole Visible“, with 10 followers connected to his profile.
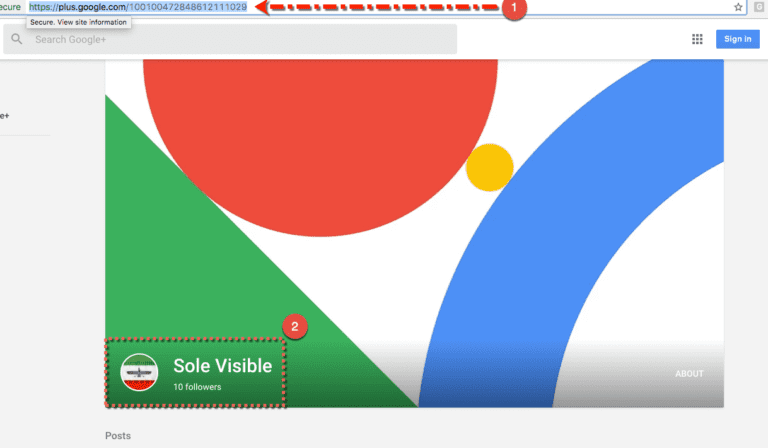
Interesting correlation and account re-use, but where can this take us? Is this a correlation to IRAN? Does this validate or verify other classifications others may have had made through information identified in malware or other artifacts in the past?
Looking a bit deeper into the picture utilized with the account, we do see a correlation to a picture depicting Persian Pride, alluding to the owner of this account being Iranian.

Pivoting on the alias – “solevisible”
In our next step, we want to also take apart the email address and look for anything related to “solevisible“. In Maltego, we create an alias, and with SocialNet, execute the SearchAllNetworks for the alias that we have connectivity to. The following leads are produced:
-
- PasteBin Account – http://pastebin.com/u/solevisible | Alias solevisible | Creation Date Time minus 3 years ago. (2014)
-
- GitHub Account – https://github.com/solevisible | Alias solevisible | Creation Time 03/26/14 .
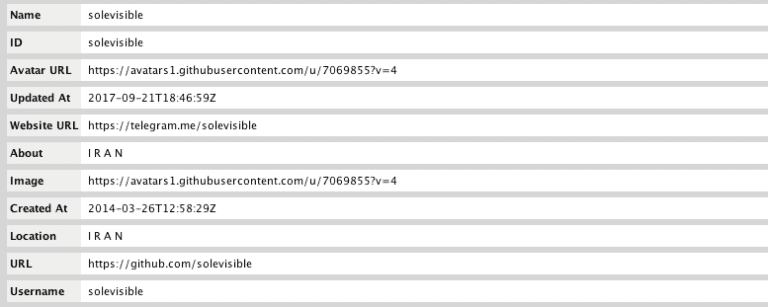
This give us clues in a few different areas, mainly other artifacts found in the GitHub and Pastebin Accounts along with associated timelines.
Within the Pastebin Account we find similar findings sighted in the Fireeye writeup, but for our purposes we want to focus on the paste where actor Sole Sad & Invisible, reference their work for Alfa Shell and solevisible shell.
#Author Sole Sad & Invisible #[email protected] #CopyRight 2014
This possibly helps us have some more insight into this email address having two actors behind this email address & Alias. Digging a bit deeper into the shout outs to “Madleets” in some of their code we see a possible birth date around 2013 for the small team.

Can we correlate “Sole Sad, Invisible aka Alfa Team to anything earlier?
The great thing about following bread crumbs is when we can find things that keep pushing us back in time. The older the data, sometimes the more valuable the data may be mixed with less operational security measures in place. Before we venture down the historical time warp we call AliasDB (Licensed Data from Zone-H, mixed with other historical alias clues). What we find are correlations between “Sole Sad and Invisible” in some of their earliest defacements, these include:
“This Hacked By ALFA.TEaM [+] [ alfa team] [+] _+_ Hacked By ALFA.TEaM [+_ H A C K E D HACKED BY ALFA TEAM WE ARE: [+++ CHIPMUNK – SOLE SAD – INVISIBLE – VERGIL – MjMAFIA … H A C K E D HACKED BY ALFA TEAM WE ARE” ( city-fun.ir 2013)
This places known aliases during 2012 (08/30/2012) of Invisible and Sole Sad to include CHIPMUNK, VERGIL, MjMAFIA (Note – MjMAFIA later drops off in later defacements on 09/05/12) .
A timeline of other sites defaced by “Alfa.TEam/Alfa Team/Alfa Team 2012”
2013-02-08 aquabluesolutions.com
2013-02-08 aasthabiocare.in
2013-02-08 ensta.in
2013-02-08 ciartindia.com
2013-02-26 flickfa.com
2013-02-27 www.omraaniha.com
2013-02-27 servicefa.com
2013-02-27 meloodiuos.ir
2013-02-27 dancefa.ir
2013-02-27 videobaran.org
2013-02-27 hacknews.ir
2013-02-27 gilansoft.ir
2013-03-14 rayansalamat.ir
2012-09-05 rankeramg.com
2012-09-05 southplacerasc.com
2012-09-05 www.autostadtwest.com
2012-09-05 www.colorsolutionsllc.com
2012-09-05 schwaia.com
2012-09-05 playagon.com
2012-09-05 amplahealth.org
2012-09-07 www.fourseasonsmanagementgroup.com
2012-09-07 mprobp.com
2012-09-08 nns.ag.gp
2012-09-12 www.chat-patogh.ir
2012-09-14 friends6flirt.com
2012-08-30 wpfarsi.com
2012-08-30 apbdays.ir
2012-08-30 city-fun.ir
2012-08-30 serverirani.com
2012-09-05 thestartrekexperience.com
2012-09-05 www.lucasenterprises.net
2012-09-05 anitashousekeeping.com
2012-09-05 pericoproductions.com
2013-02-16 webtag.org.uk
2013-02-17 www.tajfans.ir
2013-02-19 www.chatband.ir
2013-02-22 radio-tnt.com
2012-10-01 clubibericoespanol.org/backup/index_files/
2012-10-01 www.campkeystone.us/index.htm
2012-10-01 leevindesign.com/swf/
2013-01-02 www.oomid.ir
2013-01-03 www.chatabzar.ir
2013-01-10 preschool-center.ru
2013-01-12 www.defence.com.br/crm/index.html
2013-01-14 www.gu.ac.ir/Controls/index.html
2013-01-20 www.sedesign.de
2013-01-24 www.interbyte.es
2013-01-27 mehr15.com
2012-08-30 appledooni.ir
2012-08-30 fun4irani.ir
2012-08-30 asanchat.ir
2012-09-05 carterkelly.com
2013-02-08 knedusociety.org
2013-02-08 excelgrafics.com
2013-02-08 mgbhasha.com
2013-02-08 nehrdo.com
2013-02-08 qualitybrandsindia.net
2013-02-08 raviprinters.in
2013-02-08 shardultechno.com
2013-02-08 slsrc.net
2013-02-08 sakolkarlifesciences.org
2013-02-08 selfbizinfo.com
2013-02-13 www.xphost.ir
2013-02-16 anjoguardiao.com.br
Was xman_1365 and Operation Ababil related?
Who is xman_1365, what else can we find out via OSINT?
Who is solevisible @ gmail.com ? Can we find anything else about this?
Based on the indicators, can we flush out more valuable information that could be helpful for network responders, investigators ?
-
- Additional IP Addresses
-
- Additional Malware Samples
-
- Additional Campaign Time Periods
-
- Additional DNS / Domains utilized?
 Daniel Clemens
Daniel Clemens 







